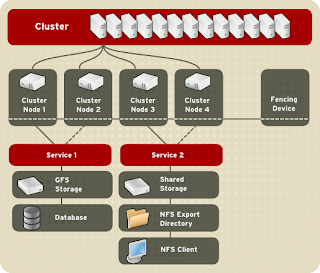
Red Hat Cluster allows you to connect a group of computers (called nodes or members) to work together as a cluster. It provides a wide variety of ways to configure hardware and software to suit your clustering needs (for example, a cluster for sharing files on a GFS file system or a cluster with high-availability service failover). This book provides information about how to use configuration tools to configure your cluster and provides considerations to take into account before deploying a Red Hat Cluster. To ensure that your deployment of Red Hat Cluster fully meets your needs and can be supported, consult with an authorized Red Hat representative before you deploy it.
skip to main |
skip to sidebar
Red Hat Cluster allows you to connect a group of computers (called nodes or members) to work together as a cluster. It provides a wide variety of ways to configure hardware and software to suit your clustering needs (for example, a cluster for sharing files on a GFS file system or a cluster with high-availability service failover). This book provides information about how to use configuration tools to configure your cluster and provides considerations to take into account before deploying a Red Hat Cluster. To ensure that your deployment of Red Hat Cluster fully meets your needs and can be supported, consult with an authorized Red Hat representative before you deploy it.
Red Hat Cluster allows you to connect a group of computers (called nodes or members) to work together as a cluster. It provides a wide variety of ways to configure hardware and software to suit your clustering needs (for example, a cluster for sharing files on a GFS file system or a cluster with high-availability service failover). This book provides information about how to use configuration tools to configure your cluster and provides considerations to take into account before deploying a Red Hat Cluster. To ensure that your deployment of Red Hat Cluster fully meets your needs and can be supported, consult with an authorized Red Hat representative before you deploy it.
Pages
THE WORLD OF COMPUTER TECHNOLOGY
Tuesday, 9 July 2013
Cluster configuration
Red Hat Cluster allows you to connect a group of computers (called nodes or members) to work together as a cluster. It provides a wide variety of ways to configure hardware and software to suit your clustering needs (for example, a cluster for sharing files on a GFS file system or a cluster with high-availability service failover). This book provides information about how to use configuration tools to configure your cluster and provides considerations to take into account before deploying a Red Hat Cluster. To ensure that your deployment of Red Hat Cluster fully meets your needs and can be supported, consult with an authorized Red Hat representative before you deploy it.
Blog Archive
-
▼
2013
(25)
-
▼
July
(15)
- HOW TO CREAT BACKDOOR IN WINDOW SEVEN
- Using Wine In Red Hat Linux
- To Password Protect Folders with Folder Protector?
- RSA Algorithm Example
- Cryptographic Algorithms
- Windows XP Network configuration
- Network configuration in Linux
- OOPs Concepts
- Setup The Timezone
- Cluster configuration
- List of web browsers
- A Comparison of Network Models
- CLOUD COMPUTING
- Basic Linux Commands
- STEGANOGRAPHY
-
▼
July
(15)
About Me
Sample Text
Sample Text
Sample text
You can replace this text by going to "Layout" and then "Page Elements" section. Edit " About "
Cluster configuration
Posted by HEMANT KUSHWAHA at 06:40 Tuesday, 9 July 2013
Red Hat Cluster allows you to connect a group of computers (called nodes or members) to work together as a cluster. It provides a wide variety of ways to configure hardware and software to suit your clustering needs (for example, a cluster for sharing files on a GFS file system or a cluster with high-availability service failover). This book provides information about how to use configuration tools to configure your cluster and provides considerations to take into account before deploying a Red Hat Cluster. To ensure that your deployment of Red Hat Cluster fully meets your needs and can be supported, consult with an authorized Red Hat representative before you deploy it.
Subscribe to:
Post Comments (Atom)
Blogroll
Blogger templates
Blogroll
Blogger news
Blogger templates
Blogger news
Powered by Blogger.
Social Icons
Social Icons
-
Less Infrastructure, More Intelligent Servers Cisco Unified Computing System (UCS) and servers unify computing, networking, mana...
-
List of web browsers History:- This is a table of personal computer web browsers by year of release of major version, in ch...
-
CISCO ROUTER SERIES The industry’s most widely deployed universal services aggregation router for enterprise and service provider ...
-
A Comparison of Network Models There are two network models that describe how networks 'work'. The OSI Model , the older model,...
-
OOPs – Object Oriented Programming System Object-oriented programming (OOP) is a programming paradigm that uses “Objects “and the...
-
HowTo: Linux Server Change OR Setup The Timezone by NIXCRAFT on AUGUST 27, 2006 · 55 COMMENTS · LAST UPDATED NOVEMBER 5, 201...
-
THE CRYPTOGRAPHY GUIDE Cryptographic Algorithms There are of course a wide range of cryptographic algorithms in use. The f...
-
RSA Algorithm Example Choose p = 3 and q = 11 Compute n = p * q = 3 * 11 = 33 Compute φ(n) = (p - 1) * (q - 1) = 2 * 10 = 20 Ch...
-
CREAT BACKDOOR :::::::::::::::::::::::::::::::::::::::::::::::::::::::::...
-
Using Wine In Red Hat Linux Wine is a great tool for Linux users who want to install and run Windows ...
Blog Archive
-
▼
2013
(25)
-
▼
July
(15)
- HOW TO CREAT BACKDOOR IN WINDOW SEVEN
- Using Wine In Red Hat Linux
- To Password Protect Folders with Folder Protector?
- RSA Algorithm Example
- Cryptographic Algorithms
- Windows XP Network configuration
- Network configuration in Linux
- OOPs Concepts
- Setup The Timezone
- Cluster configuration
- List of web browsers
- A Comparison of Network Models
- CLOUD COMPUTING
- Basic Linux Commands
- STEGANOGRAPHY
-
▼
July
(15)







.jpg)



0 comments:
Post a Comment